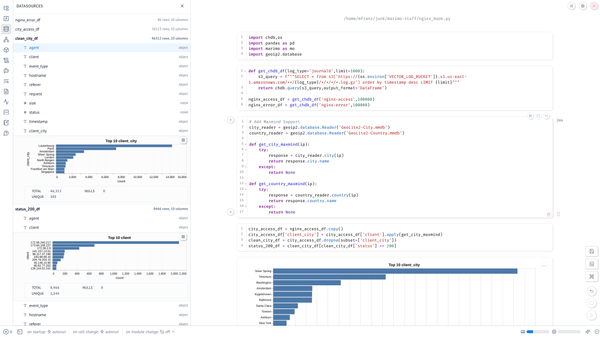
2025 Tech Learning in Review

2025 Tech Learning in Review
2025 marked the first full year where I was IC again!
For most of the year I was able to spend heads-down and hands-on without the distractions of meetings. If 2025 was the year of Kubernetes and Elasticsearch, let’s see where 2025 took me! Some of that did persist into the new year, especially Elastic, but the topics below.
(NOTE: I used gemini-cli to review my commits from cheetzsheetz but this is all humanly-written) with the top tools in each category being:
- Astral UV
- Pydantic AI
- DuckDB
- Suricata
- Trivy
- CrowdStrike FalconPy
- CryptPad
Python

Even with AI, Python is one of those things you have to do the time to keep fluency. In the beginning of 2025 I had a terrible round 2 at MongoDB for an SRE Security Lead where I totally froze on a basic Python coding problem. Fortunately, I got better but it was about spending hours each day on dedicated coding tasks.
- Marimo became a first-class tool in my notebook for exploring APIs and data.
- Pandas became my go-to tool above for slicing and dicing DataFrames in both standalone scripts and in Marimo notebooks.
- UV is now the first tool I install for managing Python and packages on Linux or Mac.
- Python Private Packages on GitLab.
- Simple Schedulers such as schedule or APSchedular when you don’t want to use something more complex like Celery.
- Asyncio is unavoidable these days due to Agent Frameworks and event loops. Get good at it.
AI

Obviously, give the pace of change in frameworks, models, and capabilities of self-hosted and SaaS models, this is tough to keep up with. I did take a bit of a break mid-year because I was burned out of working with LLMs but by the Fall I was back in the game, refreshed.
- Agent Frameworks: Agno, Pydantic, Strands, and Google ADK.
- MCP Servers where I focused on DuckDB and ClickHouse with a bit of Kubernetes at the end of the year.
- Command-Line Tools: Python-LLM and AIChat
- Agentic Editing (Zed and Gemini and Codex CLIs)
Data and Observability
As the saying say, “security is a data problem.” I spent a lot of time with SQL, mostly with ClickHouse or DuckDB but as I tried to find tools that Mac Unified Logs it led me back to some old like NXLog and Syslog-NG which provide varying levels of support. I dusted off my Vector/VRL skills.

Networking and Security
I got my start in network security and the first 15 years of my career (before I got into Cloud) was heavily focused in this space. I forgot some things and this year I had to re-learn when I had to manage Palo Alto firewalls. Routing protocols and propagation IKE Main Mode and Agreessive Mode, all these things I hadn’t touched since the Mid 2000s. I ended last year setting up a tap on my home network and right before Christmas I discovered that I had a year’s worth of Suricata data to dig into.

- IPSEC and IKE
- BGP
- Suricata
- Zeek
- Atomic Red Team
DevOps and DevSecOps

Given I took a new Cloud Security role (or at least kind of cloud security-ish) role in Apri, I had to get back some of my Terraform and Ansible skills but spent a lot of time in with container and IAC static code scanning with Trivy, which I preferred to any of the hot mess from CrowdStrike.
- European Cloud Providers like Scaleway and Exoscale
- Terraform and Bicep
- Trivy
- Ansible
- AWS CodeCommit, CodeBuild and CodeDeploy
- Gitlab CI
Security Products & Platforms

This year I used 3 different SIEM/SOAR platforms professionally (Elastic, CrowdStrike LogScale, and Google Chronicle/SecOps) but I did dip my toes into Sentinel to prepare for a job that I had multiple rounds but eventually got ghosted in January after inauguration day, when the job market seized up.
- Azure Sentinel
- CrowdStrike Vulnerability Management and Cloud Security Posture Management
- FalconPy
- Palo Alto Cloud Firewalls
- Sentinel One
- Google SecOps
Miscellaneous

As part of AI you can’t avoid the problem of web search, so I dug into the seedy (and expensive) world of web Scraping. And for my pro-Democracy tech work I set up a web site on Ghost (self-hosting) as well used (and tested local deployment) of CryptPad.